Every internet user should have firewall operations management installed on their computer. You effectively invite all hackers to violate your area and steal your sensitive papers without having them in your computers. A question comes to everyone’s mind: What exactly is a firewall? Consider it a sort of firewall between your internet and your device.
Firewall Operations Management:
Indubitably, the firewall has become a requirement of all computers, whether they are attacked by a virus, a worm, or a hacker. However, to have a deeper understanding, you must first grasp how they and computers interact. For instance, a laptop is intended to connect with other computers in its network and receive messages from the internet. Therefore, IT infrastructure managed services will work best if you want your data and information arranged productively.
Larger organizations usually have computer networks, but if you have a personal computer, it simply gets communications from the internet. Firewalls can be used in any circumstance.
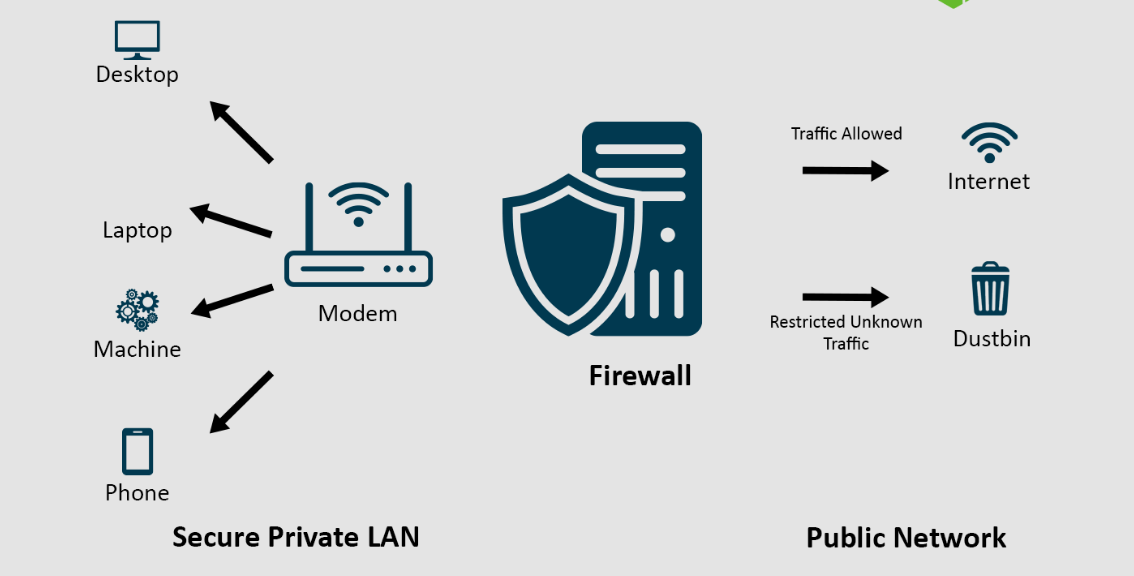
They are intended to listen in on messages transmitted between the internet and computers. They will decide which messages have access to your computer and where they can go. If a particular message does not look accurate, the computer firewall will automatically block it.
There are two types of firewalls: software and hardware. A hardware firewall is built into the machine. It monitors communications sent between the internet and devices on the network. It must be installed on your computer to function. Furthermore, it does not communicate with other machines.
It exclusively monitors communications meant for the machine on which it is installed. Hardware firewalls can monitor all computers on the same network, but software firewalls can only scan one computer at a time. Some may ask why it is necessary if you have anti-virus security on your PC. It is an excellent insight, yet both sorts of programs are required.
Altogether, firewall safety is the requirement of every computer. It makes no difference whether you work in the home or at the office. However, no one wants hackers to get access to their sensitive information. They are always on the lookout for techniques to get access to your computer and do as much harm as possible. If this is a concept that bothers you, you may always choose items that can aid you in controlling these sorts of warnings.
They also include a firewall log analyzer that may help you monitor your firewall operations management and provide reports to assist you in preventing future assaults if they occur. In addition, it offers a variety of IT management tools that may help your PC in remaining secure and productive. And in this day and age, you’ll need all the assistance you can get. For more information visit our Website.









